
Curtain DLP
Data Loss Prevention (DLP) for Enterprise Security
Curtain e-locker is a powerful Data Loss Prevention (DLP) solution that secures sensitive electronic information within an organization. It controls and monitors user actions such as saving, copying, printing, and transferring files to prevent data leakage, and ensures confidential data is accessible only within a secure zone. Users can continue working with the data within the Zone without disruption.
Whether you are in healthcare, finance, legal, or any other sector, Curtain e-locker is your trusted partner in safeguarding critical data and maintaining compliance with stringent data protection regulations.
Features
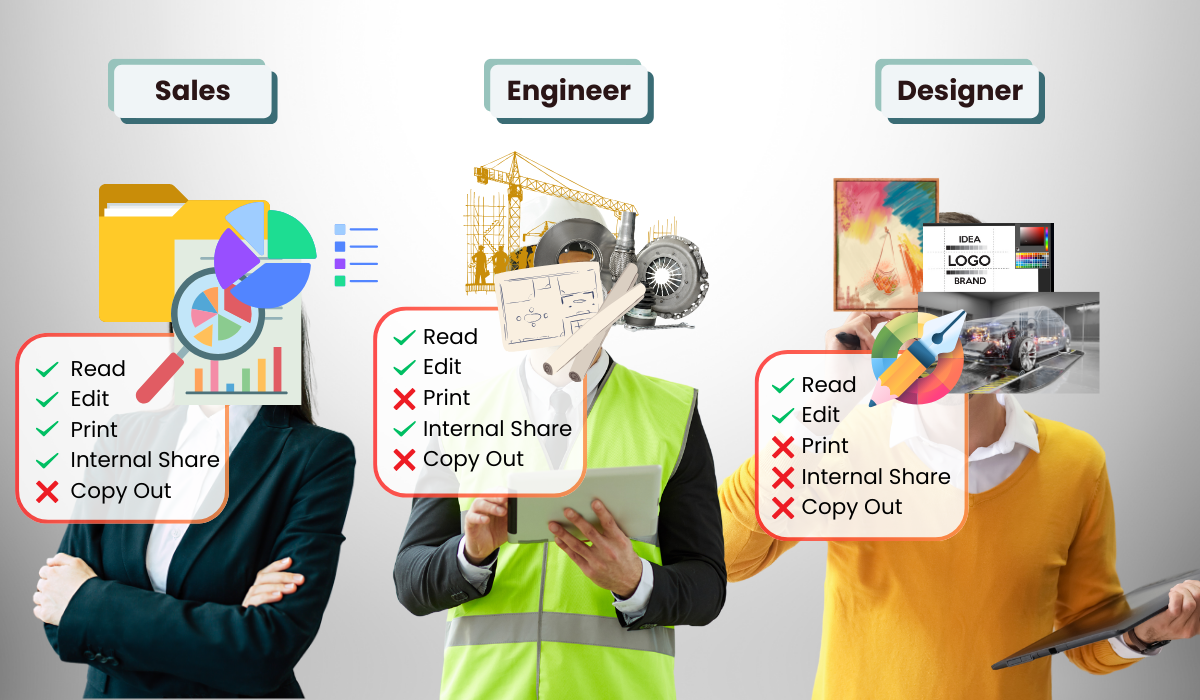
Granular User Control Over File Permissions
Curtain e-locker DLP provides precise control over user actions within the protected zone and in different folders, letting administrators manage access individually. For each user group, you can tailor permissions to specific actions, like saving, copying and pasting, sending files externally, taking screenshots, printing, editing, sharing internally, or setting it as read-only. This level of granularity ensures that sensitive information stays secure and that each user only has access to the tools they genuinely need.
Online / Offline Protection
Files can be downloaded to local Protected Directory for reading and editing.
Administrators can define different control policies, to ensure sensitive files are secure, even when workstations are offline or users are working out of the office.

Protect First Drafts
File creators must save new files to the Protected Zone
The control can be applied per application, This prevents creators from saving new design files to other unsecured locations and is especially suitable for R&D department.

Smart Copy & Paste Control
You can copy data to the Protected Zone, or copy and paste files within the Zone. However, copying data from the Protected Zone to other locations is prohibited. It strikes a good balance. between convenience and security.

Personal local protected directory
Local Protected Directory can be personalized according to logged-in user. It is suitable for shared workstations and notebooks, which prevents other users from accessing your local Protected Directory.

Screen Capture Protection
To enhance security, onscreen windows are obscured during screen captures, and screen-capture software is blocked. However, users can still enjoy the convenience of screen capture for non-sensitive data.
Additionally, administrators can apply custom watermarks to further deter unauthorized sharing.

Secure Internal File Sharing
Users can pass encrypted files to colleagues by email or USB hard disk, but they can only be decrypted within the company. Sensitive files are still secured even when the USB is lost.

Central Audit Log
File activities in the Protected Zone are logged. This allow management to review the usage of sensitive files.

Other Features
Curtain e-locker Overview
Benefits

Enhanced Data Security
Protects sensitive data from unauthorized access and leakage.

Zone-Based Protection
Allows for tailored security policies with granular control for different roles.
Real-Time Logging
Continuous logging of data flow and user activity.
Simplified Management
Easy administration with user-friendly interface for policy creation and management.

Cost-Efficient
Reduces the risk of costly data breaches and lowers compliance and regulatory costs.
Scalability
Easily scalable to accommodate different user groups and data sources.

Data Encryption
Encrypts data on the user side and in transit to ensure data integrity and confidentiality.
Supported Applications
Curtain e-locker has great support coverage on applications. It supports not only general office applications, but also CAD/CAM software, multimedia applications, ERP systems, CCTV systems, programming tools, and so on. However, if you want to secure an application which is not on our support list, please feel free to let us know. Many more software applications would be covered in days and years to come! Please check out here to see the common applications already been covered:
| Office Utilities | CAD/CAM Software | Graphics & Multimedia | Others |
|---|---|---|---|
| 7-Zip | 3ds Max | ACDSee | AXIS Camera Station |
| Adobe Acrobat | 3DVIA Composer/Player | ACDSee Pro | AXIS File Player |
| Adobe Reader | Altium Designer | ACDSeeQV Pro | Backup Player/Viewer |
| CutePDF Writer | AutoCAD | Adobe After Effects | C++ Builder XE2 |
| Google Chrome | AutoCAD Electrical | Adobe Animate | Cognos Impromptu |
| IrfanView | AutoCAD Mechanical | Adobe Bridge | Delphi XE2 |
| Microsoft Access | Autodesk Fusion 360 | Adobe Illustrator | Eclipse |
| Microsoft Edge | Autodesk Inventor | Adobe InDesign | Epicor ERP |
| Microsoft Excel | CATIA | Adobe LightRoom | File Finder |
| Microsoft Internet Explorer | CAXA CAD/Mechanical | Adobe Photoshop | Jupyter Notebook |
| Microsoft OneNote | CCAD Free/Professional | Adobe Premiere Pro | Genetec Video Player |
| Microsoft Paint | Creo | Canon XF utility | Indigo Vision |
| Microsoft PowerPoint | DWG editor/TrueView | Capture NX-D | Media Player |
| Microsoft Project | Gerber AccuMark | Corel PHOTO-PAINT | Microsoft Dynamics AX |
| Microsoft Visio | JewelCAD | CorelDRAW | Microsoft SQL Server |
| Microsoft Word | MasterCAM | HandBrake | Microsoft Visual Basic |
| Nitro PDF Pro | Matlab | JDPaint | Microsoft Visual FoxPro |
| Notepad | PADS | LaserCut | Microsoft Visual SourceSafe |
| OpenOffice | Pro/ENGINEER | LayOut | Microsoft Visual Stuido |
| PDF Complete | PTC Mathcad Prime | Media Composer | Multi Backup |
| PDFill PDF | Rhinoceros | Media player classic | Multi Sview/Viewer |
| SnippingTool | Solid Edge | OptiTex Mark | NS Backup Viewer |
| WinRAR | SolidCAM | OptiTex Modulate | Python |
| WordPad | SolidWorks | OptiTex PDS | R Studio |
| Windows Explorer | SolidWorks Composer Player | PE DESIGN NEXT | QuickBooks Premier |
| Windows Media Player | SolidWorks Electrical | PhotoImpact | SAS Enterprise Guide |
| WPS Presentation | SolidWorks Simulation | Quick Time | Smart Player |
| WPS Spreadsheets | SolidWorks EPDM | Roland 3D Engrave | SmartPSS |
| WPS Writer | Unigraphics NX | Roland Dr.Engrave | XProtect Smart Client |
| WinZip | Zhong Wang CAD | Sony Xdcam Viewer | VLC media player |
