
Mitigating Insider Threats in Document Management Systems (DMS) with Curtain e-locker DLP
Document Management Systems (DMS) such as SharePoint, HCL Notes, and Windows File Server help organizations manage and centralize critical documents: product plans, contracts, financial data, and research files. This centralization makes it easier for employees to access information, but also increases the risk if files can be freely downloaded, copied, or shared. Insider threats become harder to detect and control once documents leave the system.
The Challenge: What Happens After Access
Traditional DMS access controls focus on who can open a file. However, they do not address what users can do once the document is opened.
- Mass Data Theft: Employees may copy large volumes of sensitive files before leaving the company.
- Accidental Leakage: Important documents can be placed on personal drives, sent outside the organization, or shared with the wrong contacts.
- No Traceability: Files printed or copied onto USB drives become impossible to audit or recall.

Endpoint Vulnerabilities and Integration Needs
After download, DMS platforms lose control over files. For SharePoint, Lotus Notes, and similar systems, files brought onto desktops or laptops are outside the reach of native controls.
- Files exported from the DMS can be copied, shared, or uploaded without detection.
- Standard settings in many document platforms do not monitor or prevent copying, printing, or emailing once files reach the endpoint.
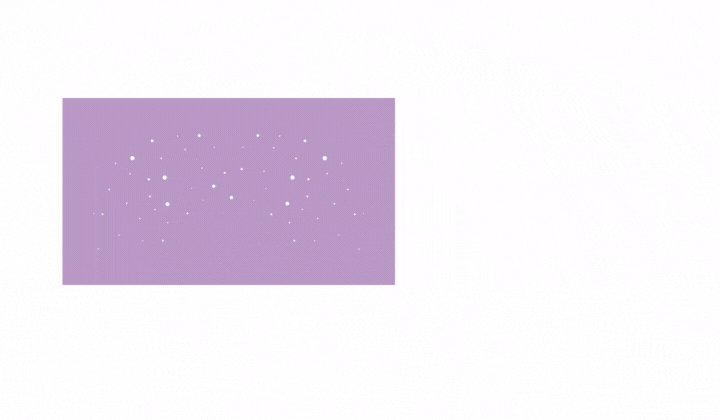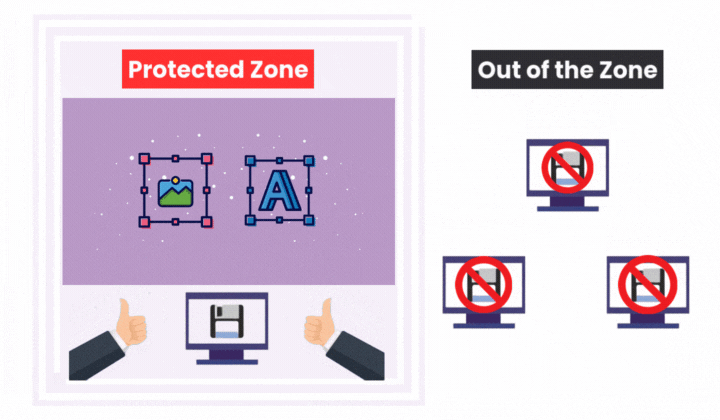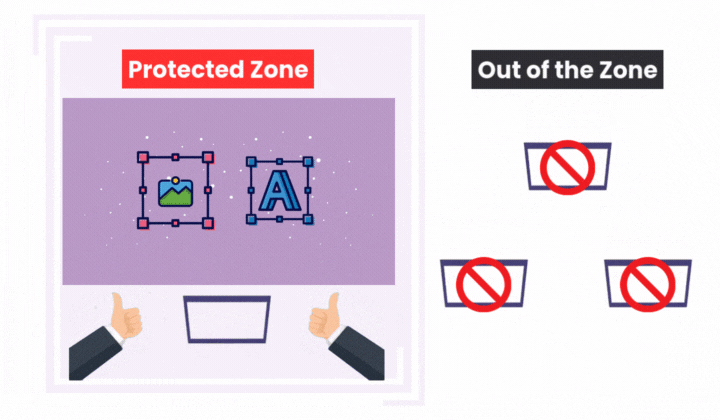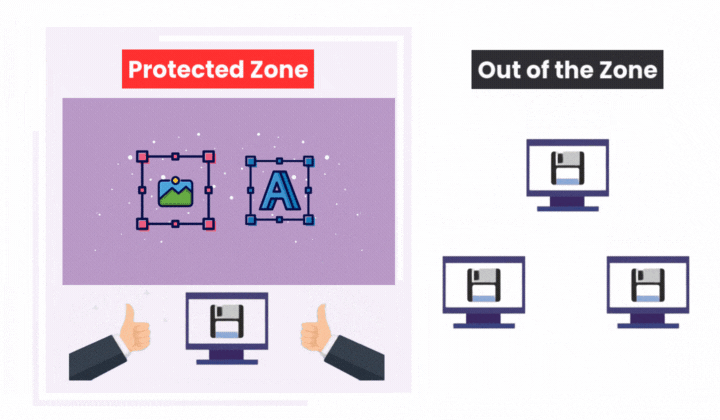

Curtain e-locker DLP: Control at the Endpoint
Curtain e-locker DLP provides controls and monitoring for DMS documents after download or access at the user’s device.

Data Outflow Control:
Blocks actions like saving to external media, exporting, printing, copy-paste, uploads to unauthorized cloud storage, and sending files via email outside approved domains.

Context-Aware Integration:
Operates with SharePoint, Lotus Notes, and Windows File Server, restricting downloads and unapproved sharing while allowing daily work.

Authorization Workflow:
Requires approval before files can be moved or sent externally, logging every action for full traceability.

Consistent Endpoint Protection:
Applies the same protections regardless of how documents are accessed—locally, via web portal, or file server.

Why Curtain e-locker DLP Is Important for DMS Security
Curtain e-locker extends data protection beyond the document repository. It ensures confidential documents remain secure once they are accessed, copied, or moved, helping organizations meet compliance needs and retain trust.

Protect Your Documents from Insider Threats
Prevent data theft, unintentional leaks, and compliance violations in your DMS—from the server all the way to the user’s desktop.
